Prep Test: Questions 181-270
Quiz Summary
0 of 19 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 19 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- Current
- Review
- Answered
- Correct
- Incorrect
-
Question 1 of 19
1. Question
Question 181
An analyst is trying to identify insecure services that are running on the internal network. After performing a port scan, the analyst identifies that a server has some insecure services enabled on default ports. Which of the following BEST describes the services that are currently running and the secure alternatives for replacing them? (Choose three.)
CorrectIncorrect -
Question 2 of 19
2. Question
Question 182
A security analyst is reviewing output of a web server log and notices a particular account is attempting to transfer large amounts of money:

Which of the following types of attack is MOST likely being conducted?
CorrectIncorrect -
Question 3 of 19
3. Question
Question 183
A privileged user at a company stole several proprietary documents from a server. The user also went into the log files and deleted all records of the incident. The systems administrator has just informed investigators that other log files are available for review. Which of the following did the administrator MOST likely configure that will assist the investigators?
CorrectIncorrect -
Question 4 of 19
4. Question
Question 184
The following are the logs of a successful attack:
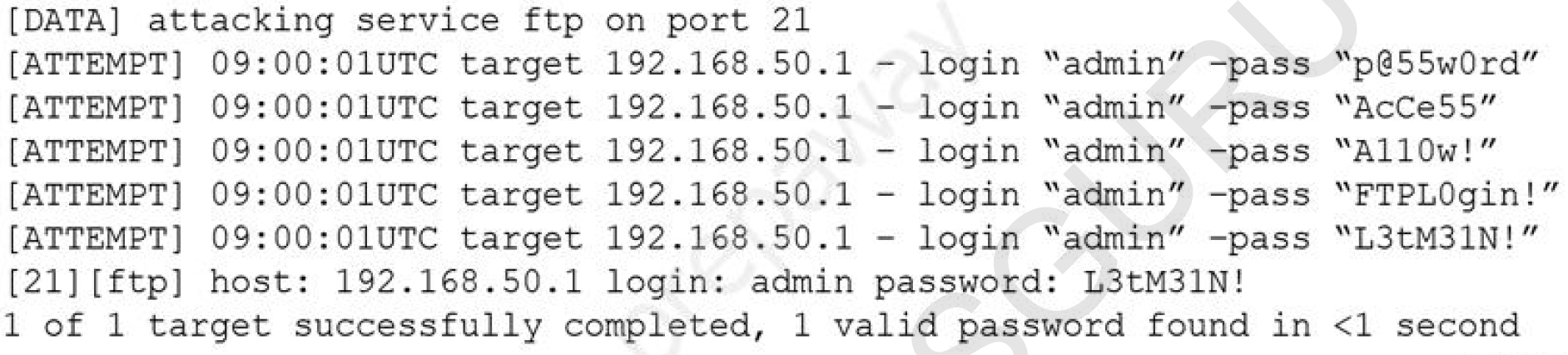
Which of the following controls would be BEST to use to prevent such a breach in the future?
CorrectIncorrect -
Question 5 of 19
5. Question
Question 185
A security administrator currently spends a large amount of time on common security tasks, such as report generation, phishing investigations, and user provisioning and de-provisioning. This prevents the administrator from spending time on other security projects. The business does not have the budget to add more staff members. Which of the following should the administrator attempt?
CorrectIncorrect -
Question 6 of 19
6. Question
Question 186
A company just developed a new web application for a government agency. The application must be assessed and authorized prior to being deployed. Which of the following is required to assess the vulnerabilities resident in the application?
CorrectIncorrect -
Question 7 of 19
7. Question
Question 187
A security analyst is performing a packet capture on a series of SOAP HTTP requests for a security assessment. The analyst redirects the output to a file. After the capture is complete, the analyst needs to review the first transactions quickly and then search the entire series of requests for a particular string. Which of the following would be BEST to use to accomplish this task? (Choose two.)
CorrectIncorrect -
Question 8 of 19
8. Question
Question 188
A company is upgrading its wireless infrastructure to WPA2-Enterprise using EAP-TLS. Which of the following must be part of the security architecture to achieve AAA? (Choose two.)
CorrectIncorrect -
Question 9 of 19
9. Question
Question 189
A university is opening a facility in a location where there is an elevated risk of theft. The university wants to protect the desktops in its classrooms and labs. Which of the following should the university use to BEST protect these assets deployed in the facility?
CorrectIncorrect -
Question 10 of 19
10. Question
Question 191
A security analyst needs to perform periodic vulnerability scans on production systems. Which of the following scan types would produce the BEST vulnerability scan report?
CorrectIncorrect -
Question 11 of 19
11. Question
Question 190
Which of the following BEST describes the MFA attribute that requires a callback on a predefined landline?
CorrectIncorrect -
Question 12 of 19
12. Question
Question 192
A worldwide manufacturing company has been experiencing email account compromises. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
CorrectIncorrect -
Question 13 of 19
13. Question
Question 193
A network administrator has been asked to design a solution to improve a company’s security posture. The administrator is given the following requirements:
✑ The solution must be inline in the network.
✑ The solution must be able to block known malicious traffic.
✑ The solution must be able to stop network-based attacks.
Which of the following should the network administrator implement to BEST meet these requirements?
CorrectIncorrect -
Question 14 of 19
14. Question
Question 194
A security administrator checks the table of a network switch, which shows the following output:
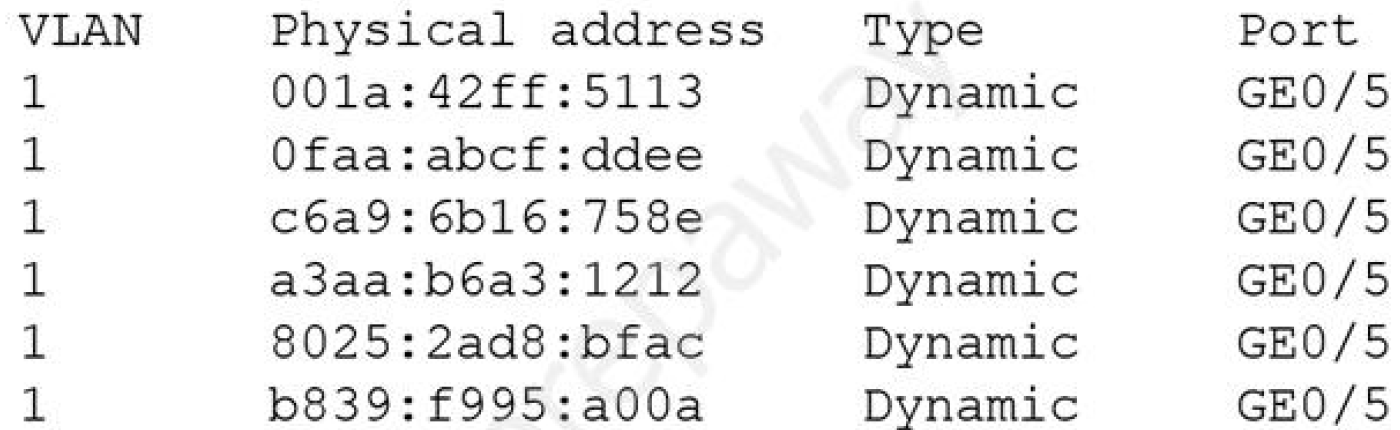
Which of the following is happening to this switch?
CorrectIncorrect -
Question 15 of 19
15. Question
Question 195
A critical file server is being upgraded, and the systems administrator must determine which RAID level the new server will need to achieve parity and handle two simultaneous disk failures. Which of the following RAID levels meet this requirement?
CorrectIncorrect -
Question 16 of 19
16. Question
Question 196
A security engineer needs to implement the following requirements:
✑ All Layer 2 switches should leverage Active Directory for authentication.
✑ All Layer 2 switches should use local fallback authentication of Active Directory is offline.
✑ All Layer 2 switches are not the same and are manufactured by several vendors.
Which of the following actions should the engineer take to meet these requirements? (Choose two.)
CorrectIncorrect -
Question 17 of 19
17. Question
Question 197
A security analyst is preparing a threat brief for an upcoming internal penetration test. The analyst needs to identify a method for determining the tactics, techniques, and procedures of a threat actor against the organization’s network. Which of the following will the analyst MOST likely use to accomplish the objective?
CorrectIncorrect -
Question 18 of 19
18. Question
Question 198
A security analyst needs to make a recommendation for restricting access to certain segments of the network using only data-link layer security. Which of the following controls will the analyst MOST likely recommend?
CorrectIncorrect -
Question 19 of 19
19. Question
Question 199
Which of the following types of controls is a CCTV camera that is not being monitored?
CorrectIncorrect
